-
Securing Microsoft: Inviting the hackers inside
Date: 12/04/07 (Security) Keywords: security, microsoft
In Part II of this series following Microsoft's security strategies, Microsoft reaches out to the security research community it once kept at a distance. This is part two in a series examining how Microsoft's security strategy has evolved over the past decade. Part 1: Securing Microsoft: From pain...
-
Master 3-D messaging security
Date: 12/04/07 (Security) Keywords: security
They're everywhere. Secure Computing's Paul Henry says you need multi-dimensional security to fend off attackers, no matter where they come from. Commentary--Messaging security is starting to resemble the world of video games. And that’s a good thing. In the 1980s and for...
-
Securing Microsoft: The next generation of security threats
Date: 12/05/07 (Security) Keywords: security, microsoft
Forget those widespread worms. Nowadays, limited-scale threats like targeted e-mail attacks are causing the most concern. The final segment in a series examining Microsoft's security strategy. Editors' note: This is Part 3 in a series examining how Microsoft's security strategy has evolved over the past decade. Part 1:...
-
Tracking tech predicted to boom in Europe
Date: 12/11/07 (Security) Keywords: technology, security
Business needs, personal security concerns will drive adoption of wireless tracking tech, says Juniper Research. Technology for wirelessly tracking vehicles and people is predicted to take off in Western Europe throughout the next five years. Business needs and personal security concerns will generate $4.85 billion in spending...
-
Real ID is bad? Compared to what?
Date: 04/05/07 (Security) Keywords: technology, security
CoreStreet founder Phil Libin says the absence of meaningful debate has hindered serious discussion about the implications of a controversial new technology. The Department of Homeland Security has published the proposed details of the Real ID act, and criticism is starting to pour in from all sides. The...
-
National ID card a disaster in the making
Date: 05/03/07 (Security) Keywords: security
Security experts Richard Forno and Bruce Schneier say Homeland Security is committing a blunder of historic proportion. Six years into the "new normal" of terror alerts, identification checks, electronic surveillance, and increasing levels of secrecy-based security, the prospect of a national identification card needs serious public debate. ...
-
Can HiTrust bring electronic health records forward?
Date: 12/19/07 (Security) Keywords: security
HiTrust (the Health Information Trust Alliance) has launched with great fanfare. Its mission is to "a common security framework for use by all parties that create, access, store or exchange personal health information." Sounds promising. Its common security framework (PDF)Â would establish...
-
Reason number 3485 why parents shouldn't be allowed to have a computer...
Date: 12/24/07 (Computer Help) Keywords: security, virus, spyware
Usually I can take care of nasty spyware thingers on my own, but this one has got me stumped.
My mom's machine runs XP, upgraded from ME [go ahead and cringe, i do it too].
She emailed me in a panic a few days ago, saying I broke her computer [bullshit], because this "internet speed monitor" thing keeps popping up.
Unfortunately, my mom doesn't know the wonders of Firefox, so she uses IE. I'm pretty certain IE is to blame, so I reinstalled Firefox [after she had uninstalled it].
She's run the CA security system scan that came with our Roadrunner broadband. It's caught quite a few things, Internet Speed Monitor being one of them.
However, when I used Firefox to try and download AVG-free and Ad-Aware, it wouldn't let me. It downloaded as some insane file extension that I don't even think exists. It's labeled as an "EFW file".
While waiting for the virus scan to finish, I checked my facebook [lolz], and this was in the place where an ad should have been:
"Removed by HIPS FW"
So now what? The virus scan is still running, and I don't have another way to get decent anti-shit programs onto this machine right now.
Suggestions? Do we just trash it? Reformat is the last thing I want to have to do, as all my mom's college coursework is on the harddrive...but I'm afraid that if I back it up on a CD, I may reinfect the fresh install.
Help? Please and thank you. :)Source: http://community.livejournal.com/computer_help/850776.html
-
Zero Day's most popular posts of 2007
Date: 12/26/07 (Security) Keywords: security, microsoft
Here's a look at the most popular posts of 2007 based on traffic. It's a microcosm of the year in security. Hacker, Microsoft duke it out over Vista design flaw Wi-Fi hacking, with a handheld PDA Super Bowl stadium site hacked, seeded with exploits ...
-
New Computer Security Conference
Date: 12/31/07 (Algorithms) Keywords: software, technology, asp, security
We are excited to announce SOURCE Boston, a new computer security conference taking place in Boston, Massachusetts on March 12-14, 2008. SOURCE combines business, technology, and software development, and provides security experts an opportunity to share ideas, insights and opportunities.
SOURCE Boston will include the following:
* An intimate setting provides opportunities for networking, focused conversations, opportunities to converse with speakers and industry thought leaders
* Top keynote speakers, including Steven Levy, Dan Geer, and Richard Clarke.
* Special VIP evening reception
* First con to combine the edginess and creativity of hacking with the professionalism of the business environment.
* First computer security conference to have a track devoted to application security
* Combines industry and professional sessions with edgy fun approaches
* First L0pht reunion in ten years
* Business track will include talks from chief executives and other key members of the management community
* SOURCE Boston is organized by key industry thought leaders, including former founders of @stake, professionally published security research experts, and former NSA employees
* SOURCE Boston takes place the week before St Patrick’s Day – one of the most exciting times to be in Boston. Additionally, the Hyatt rate will be extended into the weekend so attendees can experience Boston’s St. Patrick’s Day celebrations.
Additional speakers include:
* Matthew Moynahan, CEO of Veracode
* James Mobley, CEO of Neohapis and former CEO of @stake
* Andy Jaquith, Yankee Group
* Cedric Blancher, EADS
* Robert Martin, MITRE
* Senior Members and Founders oof Cult of the Dead Cow
* Michael Rash, Author and Security Researcher
Cost:
$895 per person
$195 student/volunteer rate
We are also looking for volunteers to assist us during the con. Please email info@sourceboston.com for more information.
HTTP://WWW.SOURCEBOSTON.COM
Please go to http://www.regonline.com/Checkin.asp?EventId=167940 to purchase tickets.
See you in March!Source: http://community.livejournal.com/algorithms/96641.html
-
If you thought 'Security '07' was hairy, just wait
Date: 01/03/08 (Security) Keywords: security
Jon Oltsik says 2008 will bring a new cluster of headlines about information security and the workplace. While you're still recovering from New Year's partying, here's something to think about: what should we expect from the world of information security over the next 12 months? In no...
-
Researcher: Firefox vulnerable to ID spoofing
Date: 01/03/08 (Security) Keywords: security
Firefox 2.0 has a vulnerability that can leave its users susceptible to an identity theft attack, according to Aviv Raff, a security researcher based in Israel. Raff outlined a bug in Firefox that allows spoofing and enables an attacker "to conduct phishing attacks, by tricking the user...
-
Microsoft plans two security bulletins; one critical impacting Vista
Date: 01/03/08 (Security) Keywords: security, microsoft
Microsoft plans a relatively light haul of two security bulletins on Patch Tuesday, but one of them is rated critical and dings Vista. Thursday's preview, which is an advance notice for folks that need to prepare for Microsoft's patches on Jan. 8, highlight two issues. ...
-
Annoying problem with security cert
Date: 01/06/08 (WebDesign) Keywords: php, browser, css, java, security
One of my sites has a Verisign certificate installed for HTTPS serving. HTTPS is configured and works fine, except for this problem.
Some pages have the proper lock & domain name in the lower right, other pages have a warning lock. Both pages are hosted with the same domain. Both pages are accessed via https://domain.net.
Secure
https://domain.net/subfolder/index.php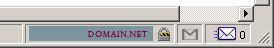
"Contains unauthenticated content"
https://domain.net/index.php
What I've done so far is to view source through my browser on the second page. Then I did alt-F and searched for http://. I found no instances of http:// on the page.
I also double clicked the lock on the second page, which brings up Firefox's Page Info window. On the Security tab there is a warning under Technical Details saying "Connection Partially Encrypted. Parts of the page you are viewing were not encrypted before being transmitted over the internet. Information sent over the Internet without encryption can be seen by other people in transit" On the Media tab several images are listed, all of which are served over https://.
There are two CSS and one Javascript includes on the second page - I confirmed that no http:// content is located in any of these.
Edit
IE displays a secure lock on the second page: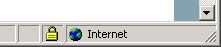
What gives?Source: http://community.livejournal.com/webdesign/1349310.html
-
First iPhone Trojan in the wild
Date: 01/08/08 (Security) Keywords: security
The long-awaited first Trojan for Apple's iPhone arrived and left its shoe print. When installed the Trojan displays the word "shoes" on the screen. The first warnings about the Trojan were posted on Saturday on the iPhone modification forum ModMyiFone.com, said security vendor F-Secure. When installed, the Trojan appeared...
-
McAfee claims open source legal concerns are much ado about nothing
Date: 01/09/08 (Open Source) Keywords: software, security
McAfee says concerns about potential open source litigation are unfounded. The company issued a statement this week to ZDNet following news this week that the security software company cited potential legal risks associated with its use of open source in its most recent annual report and letter to shareholders. Chief spokesman Joris Evers said the [...]
Source: http://feeds.feedburner.com/~r/zdnet/open-source/~3/213814067/
-
Understanding Intrusion Detection System - Samhain
Date: 01/10/08 (Java Web) Keywords: software, security, web
You never worry about your site security until after your site has been hacked for the first time. It is always a moment of truth, when you first realize how vulnerable you (your site & your data) truly are. You have probably dozens of scripts running on your server ranging from weblog software, comment form, [...]
Source: http://blog.taragana.com/index.php/archive/understanding-intrusion-detection-system-samhain/
-
Researcher finds flaw in SAP's MaxDB
Date: 01/10/08 (Data Management) Keywords: database, security, linux
A security researcher has found a remote command execution exploit in SAP's MaxDB database on the Windows, Linux and Solaris platforms. Researcher Luigi Auriemma published the flaw in MaxDB versions 7.6.03 build 007 and below. MaxDB (all ZDNet resources and SAP wiki) is an SAP-certified open source...
-
Storm worm goes phishing
Date: 01/10/08 (Security) Keywords: security
The dreaded Storm worm is now being used for phishing scams, according to security researchers. F-Secure outlined a phishing scam involving the Storm worm (all resources) on i-halifax.com and noted that the site's IP address changed every second or so--it was hosted within a botnet. ...
-
Researcher finds flaw in SAP's MaxDB
Date: 01/10/08 (Security) Keywords: database, security, linux
A security researcher has found a remote command execution exploit in SAP's MaxDB database on the Windows, Linux and Solaris platforms. Researcher Luigi Auriemma published the flaw in MaxDB versions 7.6.03 build 007 and below. MaxDB (all ZDNet resources and SAP wiki) is an SAP-certified open source...
| Previous page | || | Next page |